Introduction
Thank you for your interest in leveraging Bluebeam support for single sign-on (SSO) to enhance security, improve the user experience, and reduce support costs. The step-by-step instructions in this document will help ensure successful configuration of SSO leveraging the Microsoft OpenID Connect Protocol (OIDC) when using Okta Active Directory (Okta AD).
If you have any questions regarding these instructions, contact us.
Overview
This guide covers how to set up your SSO configuration and the information that needs to be sent to/from Bluebeam and your Okta instance.
Prepare for setup
First, you’ll need to contact Technical Support to let us know you’ll be configuring SSO. Once you’ve been added in our system, you’ll see a new option in accounts.bluebeam.com that will allow you to securely submit the necessary information.
Configure your Okta instance
To set up Bluebeam SSO with Okta:
- In the Admin Console for the Okta org that represents the Identity Provider, go to Applications > Applications.
- Click Create App Integration.
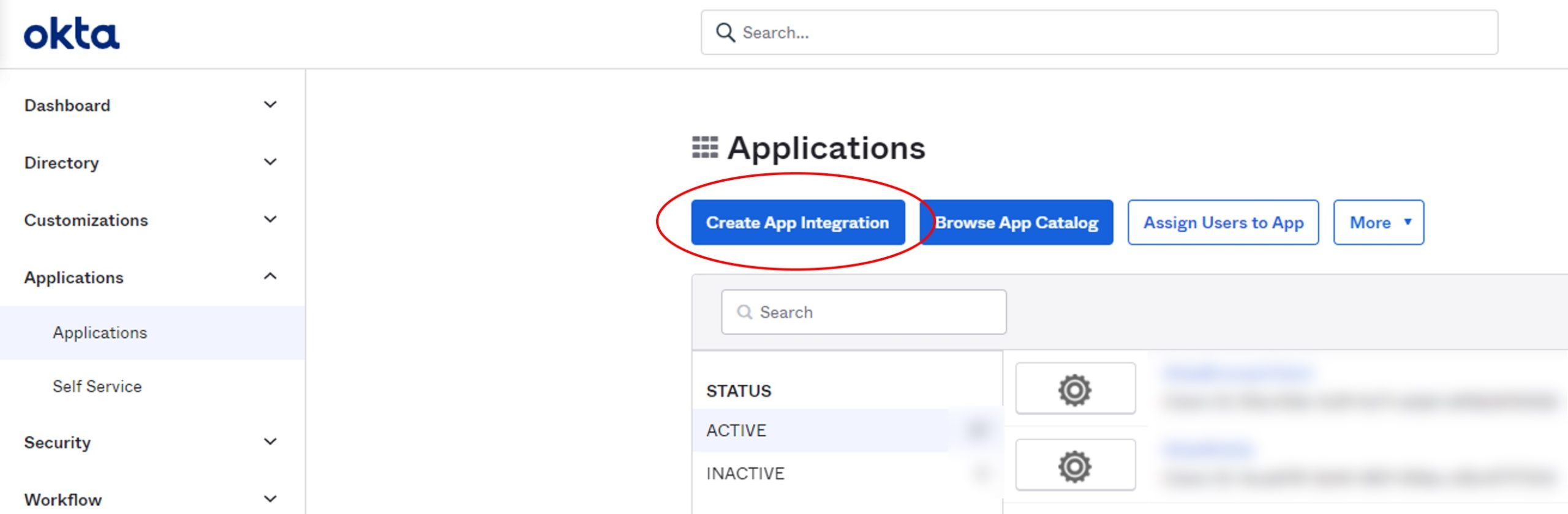
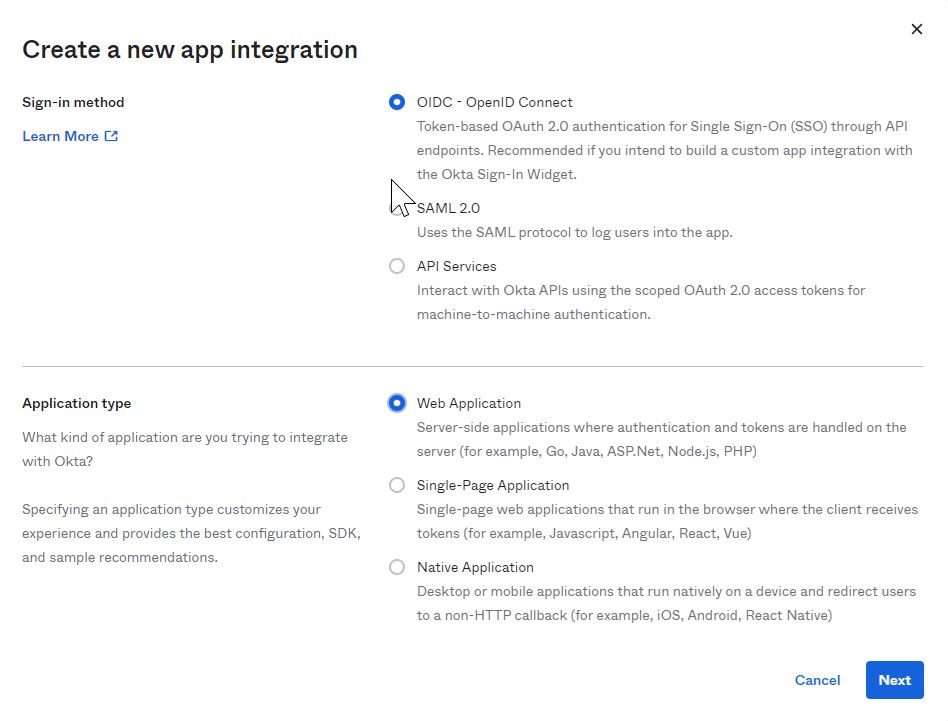
- On the Create a new app integration page, select OIDC – OpenID Connect as the Sign-in method. You need a trusted client, so select Web Application as the Application type.
- Enter a name for your application (for example, Bluebeam SSO).
- Make sure Authorization Code is selected.
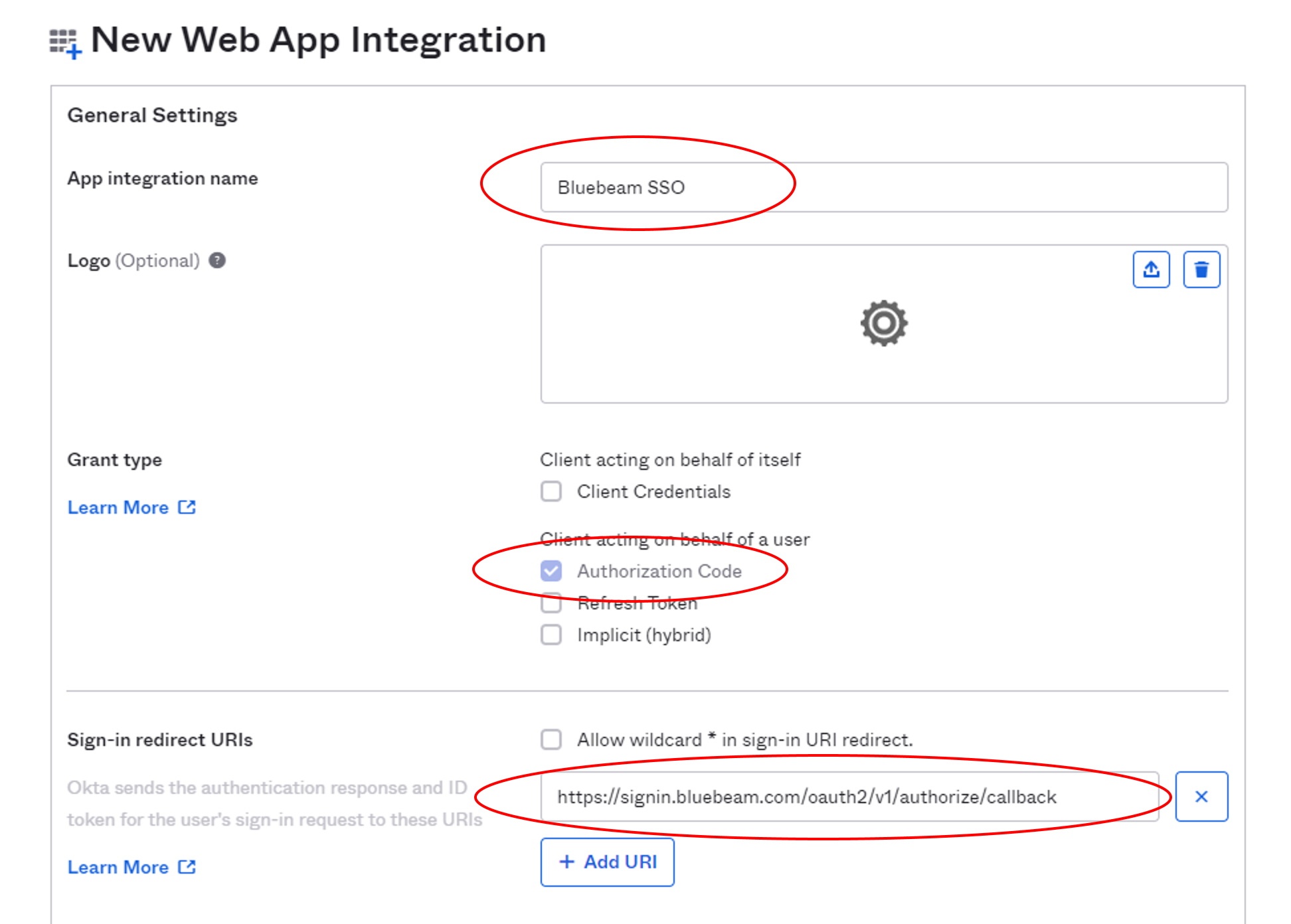
- In the Sign-in redirect URIs section, add the callback URL for your region:
Region Redirect URI U.S. https://signin.bluebeam.com/oauth2/v1/authorize/callback U.K. https://signin.bluebeamstudio.co.uk/oauth2/v1/authorize/callback Germany https://signin.bluebeamstudio.de/oauth2/v1/authorize/callback Sweden https://signin.bluebeamstudio.se/oauth2/v1/authorize/callback Australia https://signin.bluebeamstudio.com.au/oauth2/v1/authorize/callback - In the Assignments section, you can select everyone, or limit access by groups.
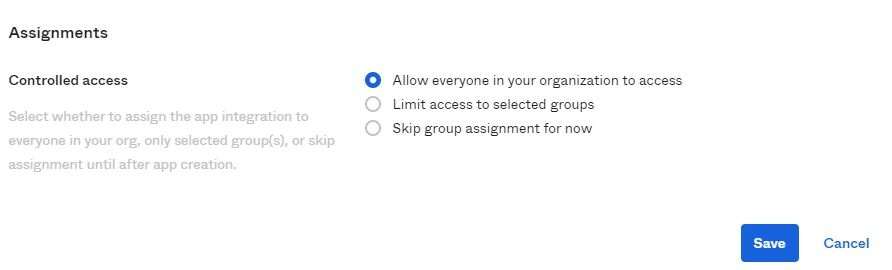
- Click Save.
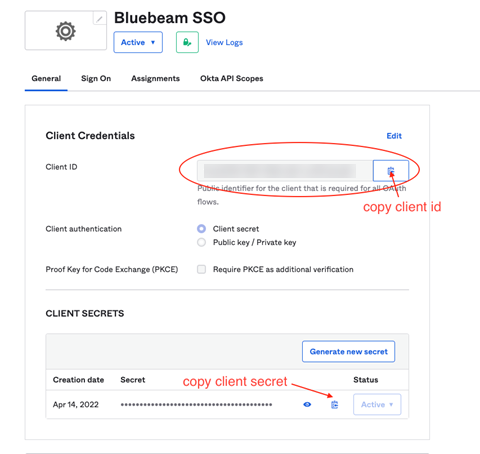
- Lastly, be sure to collect the following information for your records:
- Client ID.
- Client Secret.
- Well-known Config URL. For Okta, this appears in this form:
https://{Customer-Okta-Org-Url}/.well-known/openid-configuration
Bluebeam SSO is now set up with your Okta instance.
Submit information to Bluebeam
Once you’ve gathered all the information in the Outputs to send to Bluebeam’s systems section, you can submit them through our secure form. To submit:
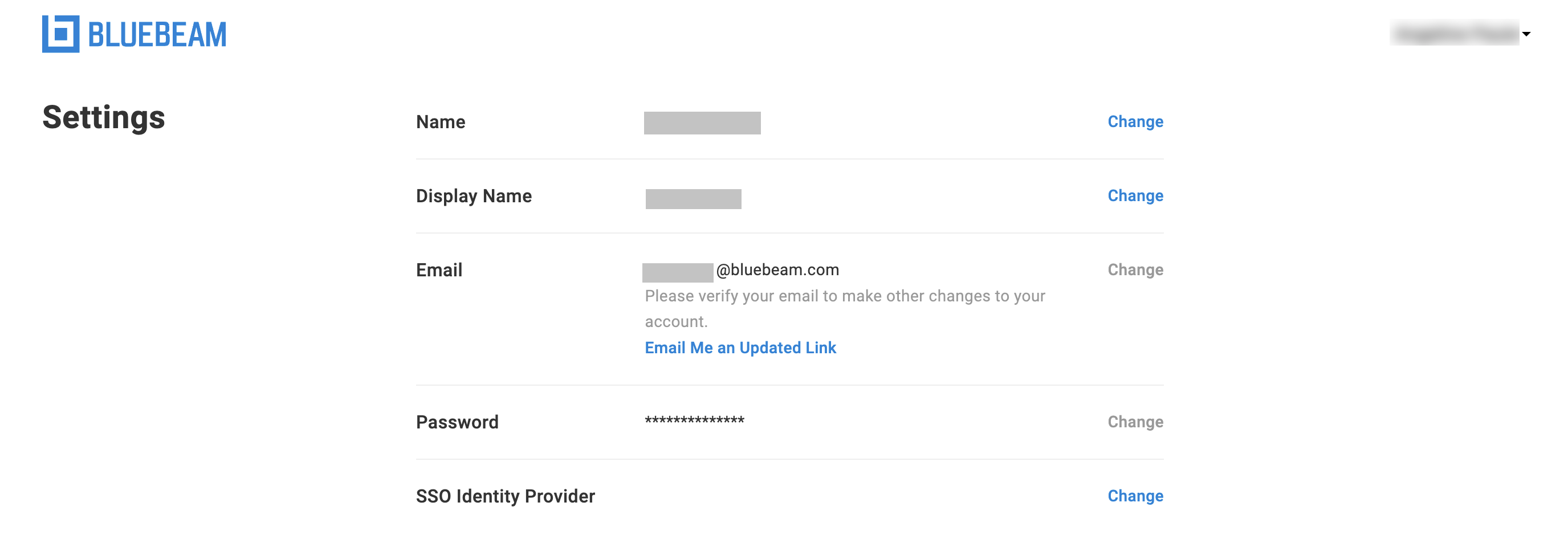
- Sign in to accounts.bluebeam.com with your BBID.
If you don’t see the SSO Identity Provider section, make sure you’re using the same BBID that you provided to Technical Support.
- Next to SSO Identity Provider, click Change.
- Select Okta as your Identity Provider. Then enter the following information about your organization:
- Company Name.
- Client Id.
- Client Secret.
- Issuer (Well-known Config URL from Step 9 above).
- Domains list (separated by commas).
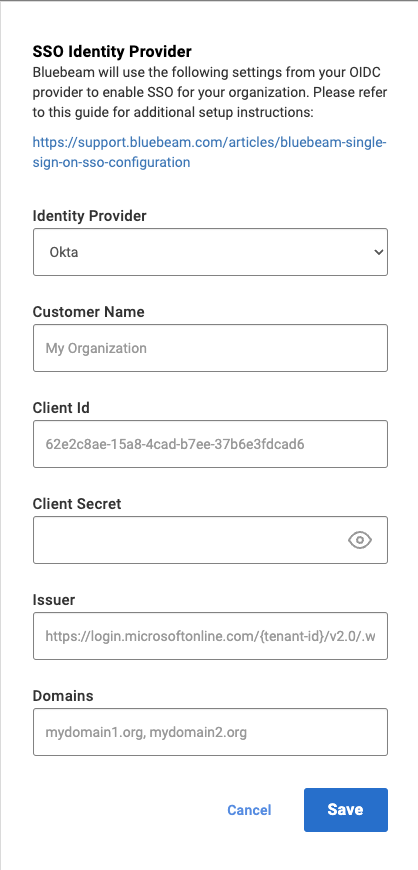 When you’re ready to configure SSO, click Save.
When you’re ready to configure SSO, click Save.
Once submitted, this information will be reviewed by our internal teams, and Bluebeam Technical Support will reach out to coordinate an activation timeline.
How-To
SSO
Revu 21
Revu 20
Revu 2019
Revu 2018
